Contents
Introduction
Artificial Intelligence (AI) has revolutionized the cybersecurity landscape, making it better at detecting and handling threats but it also brings new risks and challenges. Organizations need to know and understand the dark side of AI in cybersecurity as well to strategize their defense mechanisms more effectively. By balancing the pros and cons, businesses can use AI to boost productivity.
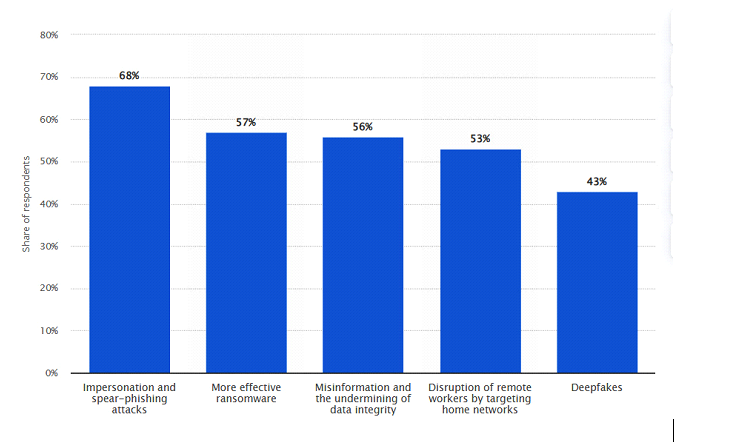
According to a report submitted by Statista, they stated, “In 2021, around 68 percent of survey respondents stated that Artificial Intelligence (AI) can be used for impersonation and spear-phishing attacks against their companies in the future. AI can also be used to enhance ransomware, which could become a real danger to companies’ IT security.”
Risks associated with AI in cybersecurity.
Malware
AI can be used to develop polymorphic malware. This type of malware possesses the ability to alter its code dynamically, making it exceedingly difficult for traditional antivirus programs to detect and neutralize it. By leveraging AI, attackers can create malware that continually evolves, enhancing its ability to evade detection and maintain persistence within targeted systems. This use of AI in cybersecurity presents challenges for professionals and underscores the dual-edged nature of AI.
Phishing
AI can create personalized phishing emails by analyzing social media profiles and other data. These targeted emails are much harder to recognize as fraudulent, significantly increasing the attacker’s success rate. As a result, individuals are more likely to fall for these scams, posing a substantial risk to businesses. This capability of AI in cybersecurity makes phishing attempts more effective and dangerous for both individuals and organizations.
Automated attacks
AI can launch automated attacks in cybersecurity with great efficiency. These attacks can operate on their own, targeting systems and disrupting services without requiring human intervention. The speed and scalability of AI-driven attacks make them very dangerous. They can quickly overwhelm networks and cause significant damage, posing a serious threat to network stability and security, highlighting the need for stronger defences against such threats.
AI model inversion
Attackers can use data poisoning to introduce harmful data into AI training sets, messing up the AI’s learning, which leads to wrong or harmful decisions. Misusing AI data can also cause biased or unethical results. Both issues weaken the reliability and effectiveness of AI systems in cybersecurity, making them less trustworthy and more prone to errors. This kind of vulnerability also leads to data privacy and compliance violations.
Surveillance
AI-driven security systems can improve surveillance, but they might invade privacy. These systems can monitor and analyze huge amounts of data quickly, raising concerns about balancing security with privacy. If used with harmful intentions, AI surveillance can also impact businesses by damaging their reputation and trust. Organizations need to handle these issues carefully and follow privacy laws to protect individual rights and maintain trust.
Complexity of AI systems
AI systems can be complex and prone to failures or misconfigurations. These issues can lead to significant security breaches if not properly addressed. Keeping AI systems reliable requires regular monitoring and maintenance to prevent malfunctions that could compromise an organization’s cybersecurity. It’s crucial to stay vigilant and fix any problems promptly to ensure the security of the system and protect against potential threats.
Ethical, legal, and bias issues
AI systems can perpetuate biases found in training data, resulting in unfair outcomes. The use of AI in cybersecurity also raises ethical and legal concerns regarding accountability and transparency. Organizations must address these issues to ensure responsible AI usage, avoiding the reinforcement of existing inequalities or legal violations. Organizations must handle these matters carefully to maintain fairness and compliance with cybersecurity practices.
AI-Driven Password Guessing/ and Cracking
AI enhances password guessing by analyzing behavior and patterns and learning from extensive datasets of compromised passwords to predict and crack them more accurately. This capability poses a significant security threat, demanding stronger authentication methods and continuous vigilance. As AI evolves, defenses follow such as implementing multifactor authentication and regular password updates to mitigate risks. Organizations with weak cyber defences must ensure the integrity of sensitive accounts and user data.
Efficiency of AI models
The efficiency of AI models, like their ability to predict and analyze patterns, can be exploited for unethical purposes. For instance, it can be used to manipulate markets or influence decision-making unfairly. This misuse highlights the need for ethical guidelines and oversight in AI development and deployment. Organizations must ensure that AI is used responsibly, with a focus on benefiting society rather than causing harm or exploiting vulnerabilities.
Conclusion
Use of AI in cybersecurity presents both challenges and opportunities. While it also introduces new risks and amplifies existing threats, it can be leveraged to enhance security measures and improve efficiency. Organizations must carefully balance the drawbacks and benefits of AI, implementing robust strategies to maximize its positive impact while mitigating potential harms.
Why Choose Sparity
At Sparity, we offer the best cybersecurity solutions to safeguard organization and enhance defense strategies. In an era of AI-driven attacks, outsmart them with Sparity’s expert solutions which utilize the same advanced AI technology to detect, prevent, and neutralize threats, ensuring organization’s digital security remains uncompromised.
Contact us now to learn more about how our expert cybersecurity solutions can benefit the businesses.
FAQs
What are the most critical cybersecurity strategies for small businesses?
Small businesses should prioritize strategies like regular software updates, employee training, strong password policies, and implementing firewalls.. Read more
What are common myths or misconceptions about cybersecurity?
Common myths include thinking only large businesses are targeted and believing antivirus software alone is sufficient protection.. Read more
What are some surprising facts about cybersecurity?
Cybersecurity incidents are on the rise, and small businesses are frequent targets, with phishing being a common attack method. Read more
How should cybersecurity be communicated to C-level executives?
Focus on business impact, risk management, and compliance to convey the importance of cybersecurity to C-level executives. Read more
What are the best practices for application security?
Practices include secure coding, regular updates, using encryption, and conducting security testing throughout the development lifecycle. Read more














